How to Recover a Hacked Social Media Account
- Nicole
- Mar 20
- 3 min read
In today’s digital world wherein social media accounts play a significant role in communication, networking, and business. But their growing dependence has also made them prime targets for hackers who seek to steal personal data, spread malicious content, or scam others using compromised profiles.
Taking back control of your hacked social media account as soon as possible is crucial to minimizing harm and safeguarding your data. This guide will provide a step-by-step process to help you recover your account, strengthen it, and ensure your online presence remains safe from future threats.
Essential Tips for Securing Your Hacked Account
Step 1: Detect the Signs of a Hack.
Check for any unusual activity that may indicate your Google account has been compromised. If there are unfamiliar login activity attempts from your Google account. Emails or messages sent from your account that you didn’t authorize. Notifications of changes to your email, phone number, or password. If you notice any of these signs, proceed to recover your account immediately.
Step 2: Navigate to the Account Recovery Page.
Use a web browser on a computer or mobile device to access the Google Account Recovery page by visiting this link.

Step 3: Enter Account Details.
On the recovery page, enter your registered email address linked to your hacked Google account. Then click “Next” to proceed.

Step 4: Enter your Password.
On the recovery page, enter the last password you remember using for your Google account. If you don’t remember your password, click “Try another way” to explore alternative recovery options. After entering your password, click “Next” to proceed.

Step 5: Get a Verification Code.
Google will send a verification code to your registered recovery phone number. If the displayed phone number is correct, click "Send" to receive the code.

Step 6: Receive and Enter the Verification Code.
A text message with a 6-digit verification code was just sent to your registered recovery phone number.
You must check your SMS inbox for the code. If you didn’t receive the code, wait a few moments or click “Try another way” for alternative recovery options.

Afterward, If you received the code, go back to your computer or mobile device and enter the 6-digit verification code on the recovery page. Then, click “Next” to proceed.

Step 7: Redirect to Your Account.
Once you've successfully entered the verification code, Google will redirect you to your account.

Step 8: Reset Your Password.
After being redirected to your account, go to “Personal info”. Under this section, you will see “Password”. Click on it to change your password.

This will redirect you to enter your latest password. After inputting your password, click “Next” to verify.

If successfully verified, it will prompt you to enter your new password. Once entered, click “Save” to complete the process.
Create a strong, unique password that you haven’t used before. Avoid using common words or easily guessable combinations.

Step 9: Review and Secure Your Account.
After recovering access, take these security measures to prevent future hacks.
Enable Two-Step Verification (2FA). Go to “Security” select "2-Step Verification" then turn it on and follow the setup process.

Review your account activity by checking “Security Activity” to identify any unauthorized logins. Remove unknown devices or sessions.
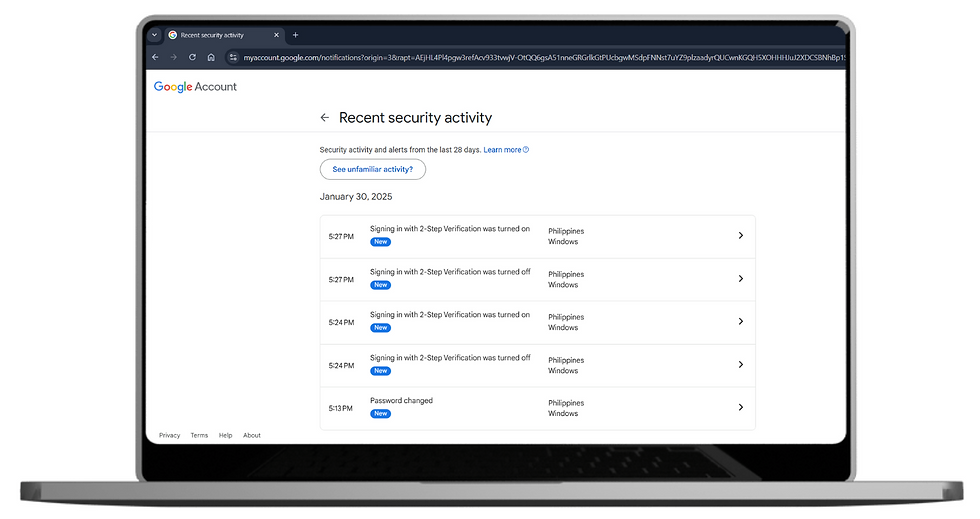
Update your recovery options to ensure your recovery email and phone number are up to date.

Step 10: Monitor Your Google Account Regularly.
To prevent future security issues enable the Google Alerts for login attempts from unknown locations. Regularly review your Google Account Security Checkup at security-checkup for updates and avoid clicking on phishing emails or suspicious links.








